System Architecture: 7 Ultimate Power Principles for Success
Ever wondered how massive tech platforms like Google or Netflix stay up and running flawlessly? It all starts with a solid system architecture—smart design, strategic planning, and scalable structure working behind the scenes.
What Is System Architecture and Why It Matters

System architecture is the blueprint of any software or technological system. It defines how components interact, where data flows, and how the entire system scales under pressure. Think of it as the architectural plan of a skyscraper—without it, even the strongest materials can’t prevent collapse.
Defining System Architecture
At its core, system architecture is the high-level structure of a system. It includes hardware, software, networks, data storage, and communication protocols. According to the ISO/IEC/IEEE 42010 standard, architecture encompasses the fundamental concepts, properties, and relationships of a system.
- It outlines components and their interactions.
- It defines interfaces and data flow.
- It ensures alignment with business goals and technical constraints.
System architecture isn’t just for tech giants—it’s essential for startups, government systems, and even IoT devices. A well-designed architecture prevents bottlenecks, enhances security, and supports future growth.
Key Components of System Architecture
A typical system architecture consists of several interconnected layers. These include:
- Application Layer: Where user-facing software operates (e.g., web apps, mobile interfaces).
- Data Layer: Manages databases, data storage, and retrieval mechanisms.
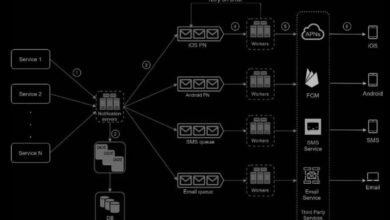
- Integration Layer: Handles communication between services via APIs, message queues, or event buses.
- Infrastructure Layer: Includes servers, cloud platforms, networking, and virtualization.
“Good system architecture is invisible—when it works, no one notices. When it fails, everyone does.” — Martin Fowler, Chief Scientist at ThoughtWorks
Types of System Architecture: From Monoliths to Microservices
Not all system architectures are created equal. The choice depends on scale, team size, deployment frequency, and business needs. Let’s explore the most common types.
Monolithic Architecture
In a monolithic architecture, all components of an application are tightly coupled and run as a single unit. This was the norm in early software development.
- Simple to develop and deploy for small applications.
- Difficult to scale independently—scaling one feature means scaling the entire app.
- High risk of cascading failures—if one module crashes, the whole system may go down.
Despite its limitations, monolithic architecture is still used in legacy systems and small-scale projects. Companies like Amazon started with monoliths before transitioning to more flexible models.
Microservices Architecture
Microservices break down an application into small, independent services that communicate via APIs. Each service handles a specific business function—user authentication, payment processing, or order management.
- Enables independent development, deployment, and scaling.
- Improves fault isolation—failure in one service doesn’t bring down the entire system.
- Increases complexity in monitoring, testing, and inter-service communication.
Netflix is a prime example of microservices done right. Their system runs on thousands of microservices, allowing rapid innovation and global scalability. You can learn more about their approach on the Netflix Tech Blog.
Event-Driven Architecture
In event-driven architecture (EDA), components react to events—such as a user placing an order or a sensor detecting motion. This model is ideal for real-time systems.
- Promotes loose coupling and asynchronous communication.
- Supports high responsiveness and scalability.
- Requires robust event management and error handling.
Uber uses event-driven architecture to manage ride requests, driver availability, and payment processing in real time. Events trigger actions across multiple services without direct dependencies.
The Role of System Architecture in Scalability and Performance
One of the primary goals of system architecture is to ensure that a system can grow without breaking. Scalability and performance are not afterthoughts—they must be designed in from the start.
Horizontal vs. Vertical Scaling
Scaling strategies are a critical part of system architecture design.
- Vertical Scaling: Adding more power (CPU, RAM) to an existing server. Simple but limited by hardware constraints.
- Horizontal Scaling: Adding more servers to distribute the load. More complex but highly scalable.
Modern cloud platforms like AWS and Google Cloud favor horizontal scaling. For example, auto-scaling groups in AWS EC2 automatically launch new instances during traffic spikes.
Load Balancing and Caching Strategies
To maintain performance under load, system architecture must include intelligent traffic distribution and data caching.
- Load Balancers: Distribute incoming requests across multiple servers to prevent overload.
- CDNs (Content Delivery Networks): Cache static content (images, videos) closer to users for faster delivery.
- In-Memory Caches: Tools like Redis or Memcached reduce database load by storing frequently accessed data in RAM.
Twitter uses a combination of load balancing and caching to handle millions of tweets per minute. Their architecture ensures low latency even during global events like the Super Bowl.
Security by Design: Integrating Protection into System Architecture
Security should never be an add-on. In modern system architecture, security is embedded at every layer—from authentication to data encryption.
Principle of Least Privilege
This principle ensures that each component or user has only the minimum access necessary to perform its function.
- Reduces attack surface.
- Prevents lateral movement in case of a breach.
- Implemented via role-based access control (RBAC) or attribute-based access control (ABAC).
Google’s BeyondCorp model eliminates the concept of a trusted internal network, enforcing strict access controls regardless of user location.
Data Encryption and Secure Communication
Data must be protected both at rest and in transit.
- Encryption at Rest: Data stored in databases or disks is encrypted using AES-256 or similar standards.
- Encryption in Transit: HTTPS (TLS/SSL) secures communication between clients and servers.
- Secrets Management: Tools like HashiCorp Vault or AWS Secrets Manager protect API keys and credentials.
A breach at Capital One in 2019 highlighted the importance of proper configuration and encryption. A misconfigured firewall allowed unauthorized access to sensitive customer data.
“Security is not a feature. It’s a culture embedded in system architecture.” — Bruce Schneier, Security Technologist
Cloud-Native System Architecture: The Future of Scalable Systems
The rise of cloud computing has revolutionized system architecture. Cloud-native design leverages cloud platforms to build resilient, scalable, and agile systems.
Containers and Orchestration with Kubernetes
Containers package applications and dependencies into isolated units, ensuring consistency across environments.
- Docker is the most popular containerization platform.
- Kubernetes automates deployment, scaling, and management of containerized applications.
- Enables CI/CD pipelines and blue-green deployments.
Spotify uses Kubernetes to manage thousands of microservices, enabling rapid feature releases and efficient resource utilization.
Serverless Architecture
Serverless computing allows developers to run code without managing servers. Providers like AWS Lambda or Google Cloud Functions handle infrastructure automatically.
- Pays only for execution time—cost-effective for sporadic workloads.
- Scales automatically with demand.
- Limited execution duration and cold start latency are key challenges.
Adobe uses AWS Lambda to process image uploads in real time, reducing operational overhead and improving user experience.
Designing for Resilience: Fault Tolerance and Disaster Recovery
No system is immune to failure. A robust system architecture anticipates failures and ensures continuity.
Redundancy and High Availability
Redundancy means having backup components ready to take over if the primary fails.
- Multi-region deployments ensure availability during regional outages.
- Replicated databases (e.g., PostgreSQL with streaming replication) prevent data loss.
- Load balancers detect failed instances and reroute traffic.
Azure’s availability zones provide physically separate data centers within a region, minimizing downtime risks.
Disaster Recovery and Backup Strategies
Disaster recovery (DR) plans are essential for business continuity.
- Backup Frequency: Daily, hourly, or real-time backups based on data criticality.
- Recovery Point Objective (RPO): Maximum acceptable data loss (e.g., 5 minutes).
- Recovery Time Objective (RTO): Time to restore operations after failure.
Dropbox uses a hybrid cloud strategy with multiple backup layers, ensuring user files are recoverable even after catastrophic failures.
Best Practices for Building a Modern System Architecture
Creating a successful system architecture isn’t just about technology—it’s about process, collaboration, and foresight.
Start with Clear Requirements and Use Cases
Before writing a single line of code, define what the system must do.
- Identify user personas and workflows.
- Map out non-functional requirements: scalability, latency, security, compliance.
- Use tools like user stories or use case diagrams to visualize needs.
Failure to define requirements led to the Healthcare.gov launch disaster in 2013, where poor architecture caused system crashes during peak enrollment.
Adopt Iterative Design and Prototyping
Architecture isn’t set in stone. Use iterative design to test assumptions early.
- Build proof-of-concept (PoC) systems to validate technologies.
- Use architectural decision records (ADRs) to document key choices.
- Refactor and evolve the architecture as the system grows.
Amazon’s two-pizza team rule—teams small enough to be fed with two pizzas—encourages modular design and faster decision-making.
Monitor, Measure, and Optimize Continuously
Even the best system architecture needs ongoing tuning.
- Implement observability with logging, monitoring, and tracing (e.g., Prometheus, Grafana, Jaeger).
- Set up alerts for anomalies in latency, error rates, or resource usage.
- Use A/B testing to evaluate architectural changes.
LinkedIn uses a real-time monitoring dashboard to track system health across its global infrastructure, enabling rapid response to issues.
What is system architecture?
System architecture is the structural design of a system, defining how its components interact, how data flows, and how it meets technical and business requirements. It serves as a blueprint for development, deployment, and maintenance.
Why is system architecture important?
It ensures scalability, reliability, security, and maintainability. A well-designed architecture reduces technical debt, supports agile development, and enables long-term success.
What are the main types of system architecture?
The main types include monolithic, microservices, event-driven, service-oriented (SOA), and serverless architectures. Each has trade-offs in complexity, scalability, and team coordination.
How does cloud computing impact system architecture?
Cloud computing enables elastic scalability, managed services, and global reach. It promotes cloud-native patterns like containers, serverless, and infrastructure-as-code (IaC), transforming how systems are built and operated.
What tools are used in system architecture design?
Common tools include UML (Unified Modeling Language), C4 model for visualizing software architecture, architecture decision records (ADRs), and platforms like AWS, Azure, or Google Cloud for implementation and simulation.
System architecture is the invisible foundation of every successful digital product. From defining structure to enabling scalability, security, and resilience, it shapes how systems behave under real-world conditions. Whether you’re building a startup MVP or a global enterprise platform, investing in robust system architecture pays dividends in performance, reliability, and agility. The principles covered—modularity, cloud-native design, security by default, and continuous optimization—are not just best practices; they’re necessities in today’s fast-evolving tech landscape.
Further Reading: